



In the era of rapid digital transformation, safeguarding organizational assets against evolving cyber threats is paramount. "Empowering Digital Resilience: Innovative Cybersecurity Solutions for Modern Challenges" encapsulates our commitment to staying one step ahead in the cybersecurity landscape. We offer a suite of cutting-edge solutions designed to fortify the digital infrastructure of businesses against an array of sophisticated threats. From advanced threat detection and real-time monitoring to robust encryption protocols, our innovative cybersecurity solutions are tailored to address the complexities of modern challenges. By harnessing the latest technologies and employing proactive strategies, we empower organizations to build and maintain digital resilience in the face of an ever-changing threat landscape. Our commitment is not only to protect against current cyber threats but also to anticipate and mitigate future risks, ensuring that businesses can navigate the digital landscape with confidence and security.
Experts

Projects delivered

Global Clients
NVISH’s advanced threat detection capabilities that employ technologies to identify and neutralize a wide range of cyber threats, from malware and phishing attacks to zero-day vulnerabilities.

Experience the power of real-time monitoring, enabling swift response to potential security incidents. Our solution provides continuous surveillance to mitigate risks promptly.

Protect every endpoint within your network with our robust security solutions, ensuring that devices and systems are shielded from potential cyber threats.
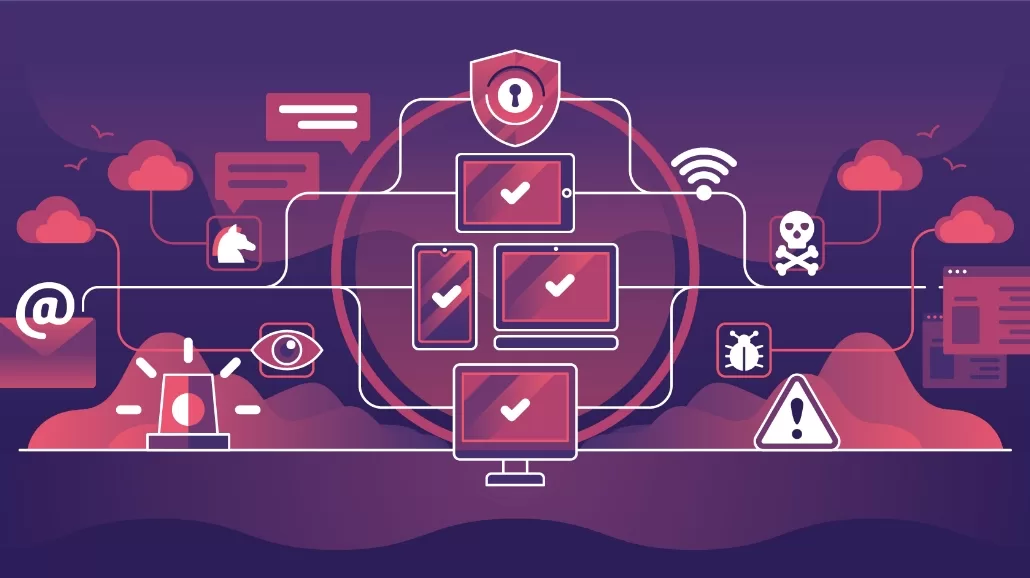
Implement secure access controls to manage user permissions and restrict unauthorized access, safeguarding critical systems and sensitive data.

Safeguard your data with state-of-the-art encryption protocols, ensuring that sensitive information remains confidential and protected against unauthorized access.

Develop a comprehensive incident response plan with our expertise, ensuring that your organization is well-prepared to handle and recover from cybersecurity incidents effectively.

Enhance your organization’s cybersecurity posture by investing in our tailored security awareness training programs, educating employees on best practices and potential threats.

Fortify your network infrastructure against cyber threats with our network security solutions, including firewalls, intrusion detection systems, and secure configuration protocols.

Stay secure with Continuous Vulnerability Assessments. We monitor your systems around the clock, identifying and patching vulnerabilities in real time. Proactive defense for constant peace of mind.

Navigate regulatory landscapes with ease. Our Compliance Assurance ensures constant adherence to industry standards. Stay updated, mitigate risks, and confidently meet compliance requirements, safeguarding your business integrity.

Comprehensive Solutions: NVISH offers a wide range of cybersecurity services, covering everything from risk assessment to threat detection, leveraging a team of seasoned experts.

Cutting-edge Technology: Stay ahead of evolving threats with NVISH’s innovative approach, utilizing the latest technologies and methodologies to safeguard your digital assets.
Continuous Monitoring: NVISH provides proactive cybersecurity measures with continuous monitoring, ensuring early threat detection and swift response to potential risks.

Tailored to Your Needs: Every organization is unique. NVISH crafts customized cybersecurity solutions, aligning with your specific business requirements and industry regulations.
Trusted Partner: Choose NVISH as your cybersecurity ally for reliability and trust. With a track record of successful implementations, we prioritize your security, allowing you to focus on your core business functions.

In the ever-expanding digital landscape, the significance of a robust Cybersecurity Methodology cannot be overstated.

Explore our proactive approach to gathering and analyzing threat intelligence, enabling the identification of potential cyber threats before they impact your organization.

Understand our methodology for conducting dynamic risk assessments, identifying vulnerabilities, and implementing strategic mitigation measures to reduce overall risk exposure.

Adaptive Security Architecture: Intelligent, agile, and proactive defense. Continuously evolving to counter dynamic cyber threats. Scalable, collaborative, and resilient, ensuring robust protection for modern digital landscapes.

Delve into our methodologies for real-time incident detection, rapid response, and effective containment, minimizing the impact of security incidents on your organization.
Explore our approach to continuous monitoring, ensuring ongoing compliance with industry standards and regulatory requirements while maintaining a vigilant stance against potential threats.

Understand how our methodology includes robust access controls and privilege management, ensuring that only authorized individuals have access to sensitive systems and data.

Learn about our strategies for fostering a cybersecurity-aware culture within your organization through regular training programs, keeping employees informed and vigilant.

Explore our methodology for timely patch management and system updates, minimizing vulnerabilities and ensuring that your systems are equipped with the latest security enhancements.

Understand our focus on encryption and data protection, safeguarding sensitive information from unauthorized access and ensuring the confidentiality of critical data assets.

Explore our collaborative governance approach, where we work closely with your organization to establish and maintain effective cybersecurity policies, procedures, and compliance frameworks.
We use top-notch tools to fine-tune your campaigns and achieve exceptional success in reaching your desired audience.
With over 20+ active clients across various industries, serving 100+ global clients, and 18+ years of experience, we have a proven track record of providing exceptional digital services to some of the world's leading organizations, including those in the USA, India and across the globe.